“It's a service that is not always appreciated until it's needed but then it becomes a life-saver!” – SES Secure Client.
When considering whether to implement Escrow for software, which also known as Software Escrow and Source Code Escrow, it's common for people to focus on how unlikely a disruption event may seem. This often prompts the question of “is Software Escrow really necessary?”. While this hesitation is understandable, it's important to also recognise that the cost, complexity, and stress of recovering from an unexpected disruption, when no risk mitigation procedures are in place, can far outweigh the effort of proactively establishing a business continuity plan before issues arise.
Escrow in the Context of Software
The term Escrow is used across the globe in a range of various contexts. It commonly refers to a financial agreement in which a neutral third-party holds funds involved in a transaction between two parties. These funds are released when certain conditions have been met. Escrow in the context of software refers to a risk mitigation tool known as ‘Software Escrow’.
In today’s business landscape, software forms the backbone of operations, making it essential for ensuring the successful running of a business. You may be thinking, so, what’s the actual purpose of Software Escrow? Well, Software Escrow is a risk mitigation tool that addresses third-party risk. For businesses that rely on critical software applications that are provided by third-party software vendors, situations such as the vendor going bankrupt, the vendor facing maintenance issues, or the vendor breaching the terms of an agreement could lead to an end-user losing access to critical applications.
A Software Escrow Solution is able to manage this risk through providing a means for the end-user to continue accessing and maintaining a critical software application.
Software Escrow is an effective risk mitigation tool for businesses of sizes and statures. It supports those that are seeking to optimise their business continuity capabilities and ensure that appropriate procedures are in place if an unforeseen issue arises.
How Does Source Code Escrow Work?
In the Software Escrow space of today, there are a range of different solutions that are available. Once an Escrow provider has determined the right solution for a client’s specific needs, requirements, and preferences, an agreement is set up. After the terms of the agreement have been agreed upon by all parties, the end-user deposits source code and other materials with the Escrow provider. These materials determine the features, behaviour, and functionality of a given software application.
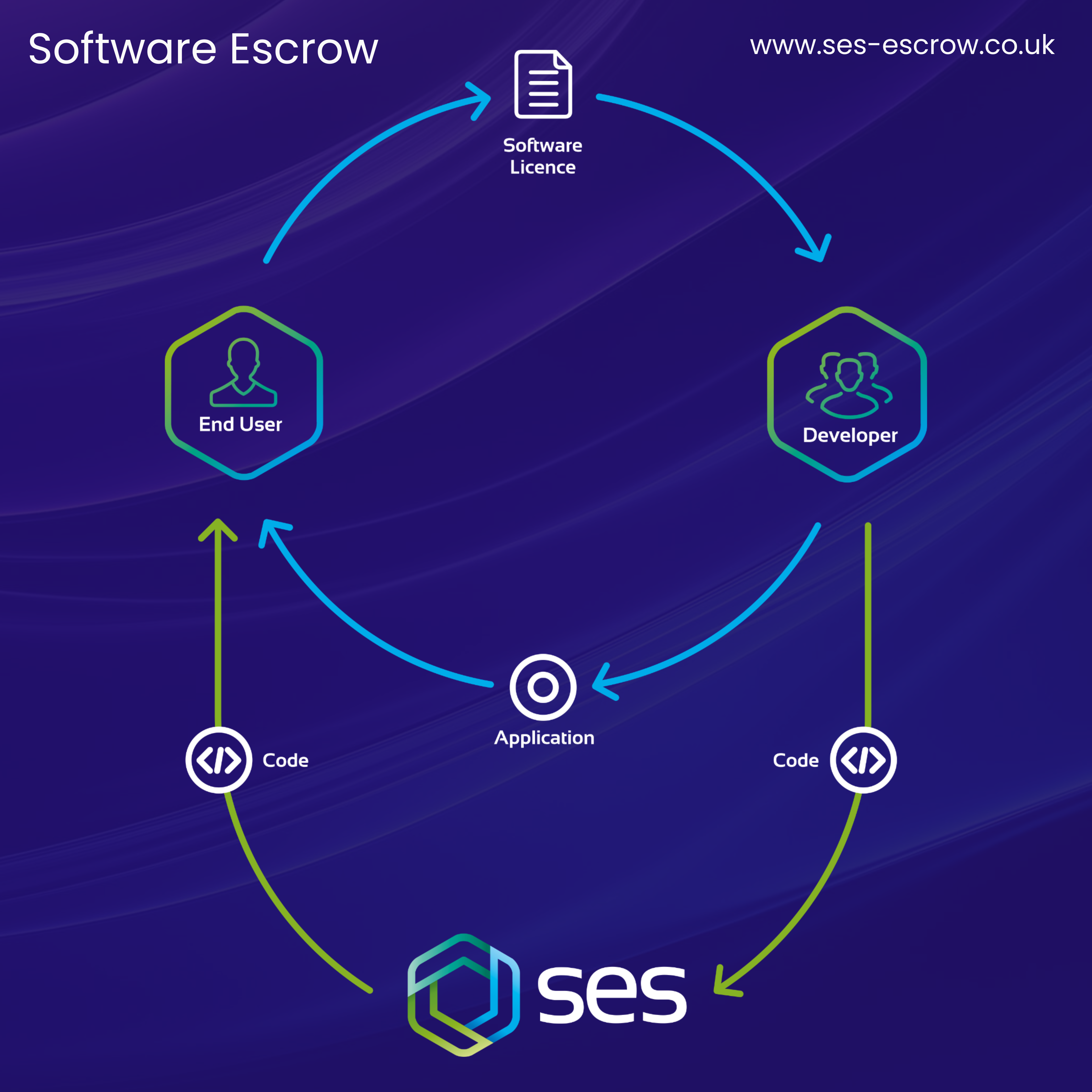
After the initial deposits have been made, the Escrow agent performs a series of tests to verify that the materials are both accurate and current. Additional deposits may be submitted to reflect any updates to the software application. This process ensures that, in the event of a source code release, the most recent version of an application is readily available.
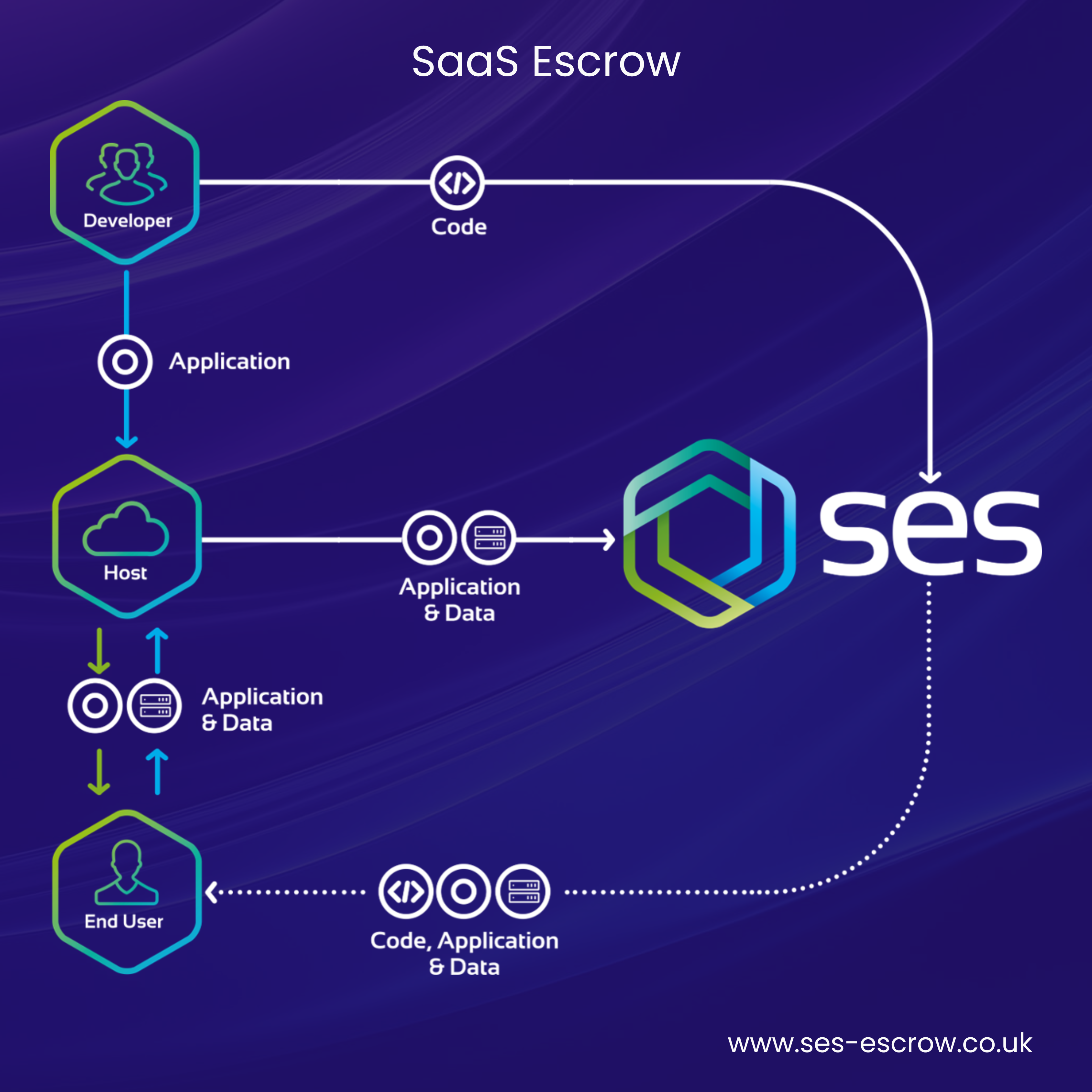
As shown above, alongside Traditional Software Escrow, SES Secure also provide Software Escrow for SaaS applications.
Working with SES
To understand how our team can support you with your risk mitigation strategy, please get in touch. To date, we’ve supported over 3,000 clients from across more than 45 countries. We also have over 200 verified client reviews on Feefo. Check them out here.