Source Code Escrow, also known as Software Escrow and Escrow for Software, is a tri-party legal agreement that ensures that a critical software application is always accessible and protected.
When Source Code Escrow was initially introduced, it was used for mitigating software risk associated with applications that were physically installed on the premises of a business. However, modern day Software Escrow services can also safeguard cloud-hosted (SaaS) applications.
At present, Escrow for Software can support and protect:
Source Code Access in Critical Applications
If a software vendor, also known as a software supplier, faces disruption, an end-user’s access to source code may become jeopardised. In such a situation, the activation of a Software Escrow solution would enable an end-user to continue operating and maintaining the software application in question. Common examples of events that may result in the activation of a Source Code Solution include a vendor going out of business, a vendor failing to maintain the software, and a vendor breaching an agreement.
Business Continuity
Escrow for Software forms a foundational pillar for a business’s risk management and operational resilience strategy. Ultimately, it ensures that an end-user (the licensee) can keep their operations running, even when vendor disruption occurs.
Intellectual Property Protection
Software vendors can ensure the protection of their IP by allowing source code to only be released when specific conditions have been met. These conditions are widely referred to as ‘release conditions’ or ‘release triggers’.
Compliance and Risk Management
The implementation of a Source Code Escrow solution can protect against risks associated with the failure of complying with regulatory or contractual requirements. In industries such as finance and government, misalignment with such guidelines can lead to strict penalties.
Trust and Transparency
A Software Escrow agreement builds confidence between all parties involved. It’s key to consider that Software Escrow does not question or dismiss the impressive capabilities of software vendors, instead it ensures that plans are in place to effectively manage any unforeseen obstacles.
It’s also important to address the ability of the Software Escrow model to manage reputational damage and financial loss. These are two potential outcomes that may occur if access to a critical software application is interrupted and no risk mitigation procedures are in place. With this in mind, Source Code Escrow is able to instil a great deal of confidence and trust within all involved parties.
Protection of Updates
The Source Code Escrow process involves the end-user depositing source code and other relevant materials with an escrow agent (SES Secure). In line with any updates that are made to these materials, the materials held in Escrow are also be updated. This guarantees that, in the event of a Source Code release event, the materials provided reflect the most current version available.
All of the following can be placed in Escrow:
- Build instructions and documentation.
- Third-party dependencies.
- Configuration files.
- Encryption keys.
- Virtual machines or containers.
Is Escrow for Software Really Worth It?
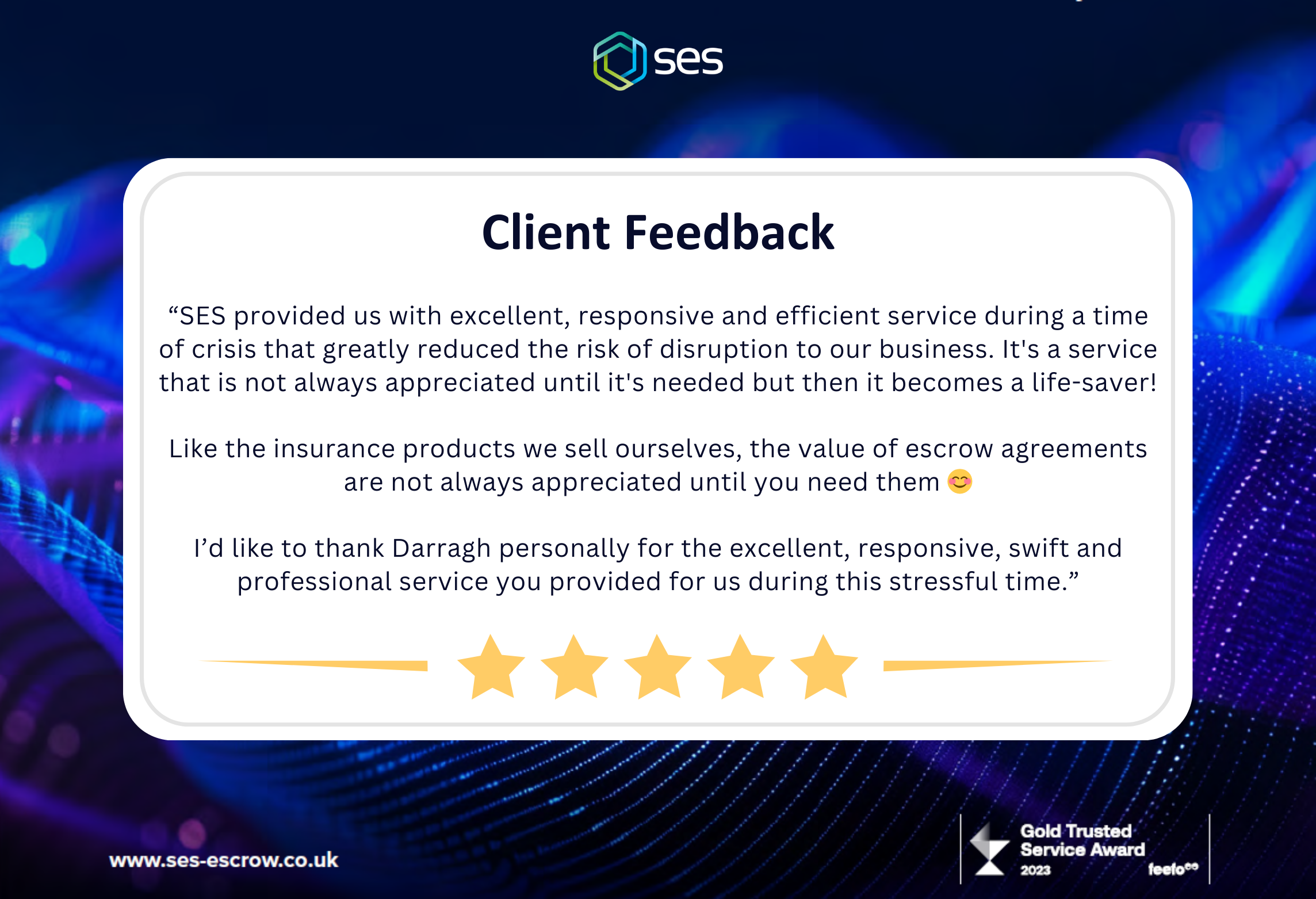
When deciding whether or not to implement Software Escrow, many people contemplate on the unlikeliness of a disruption event happening. This leads the question of ‘is Software Escrow worth it?’ being asked. Whilst this is completely understandable, it’s also crucial to consider that the cost, hassle, and stress involved in recovering from a disruption event or disaster in the absence of risk mitigation measures, is significantly greater than that of establishing a plan well in advance to any potential obstacles developing.
To learn more, check out our blog, ‘Is Software Escrow Worth It?’.
Working with SES
To understand how our team can support you with your risk mitigation strategy, please get in touch. To date, we’ve supported over 3,000 clients from a cross more than 45 countries. We also have over 200 verified client reviews on Feefo. Check them out here.