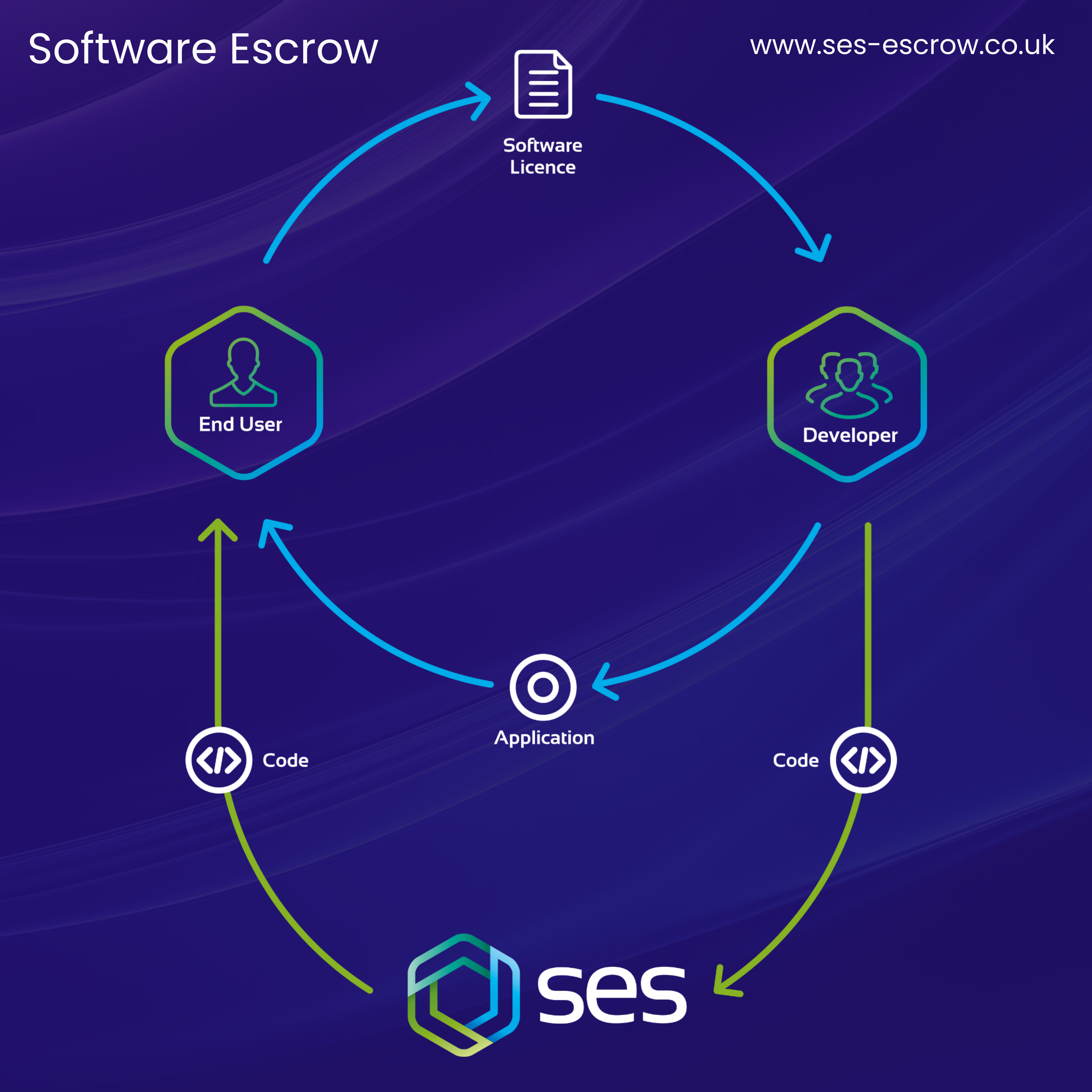
A Source Code Escrow Agreement, also widely known as a Software Escrow Agreement is a tri-party legal agreement. In the simplest of terms, the purpose of this agreement is to ensure the continuity of critical business applications, even during disruption events.
What is Software Escrow?
Before delving into the actual agreement aspect of the Software Escrow model, we must first look at what Software Escrow (Source Code Escrow) actually is. Software Escrow is a risk mitigation tool that was first introduced in the 1980’s. This period of time saw a substantial spike in the popularity of software systems. However, alongside this growth in software usage was a rising level of third-party risk stemming from the third-party software providers that were supplying software to various companies.
In response to growing concerns, Software Escrow was brought in as a risk mitigation tool, one that safeguarded end-users from the risks faced by their software suppliers, such as the suppliers going bankrupt or encountering maintenance issues.
The world of Source Code Escrow can certainly be an overwhelming place - for a simple and easy-to-follow breakdown on it, check out our blog, 'A Beginner’s Guide to Software Escrow'.
The Parties Involved in a Source Code Agreement
As mentioned at the start of this blog, a Source Code Agreement concerns three parties. These are:
1. The end user (the end-user of the application)
The end user, often a business or an organisation, relies on software to support critical operations. When entering a Source Code Escrow Agreement, an end-user's primary concern is usually business continuity.
So, what happens if their software vendor goes out of business, fails to maintain the software, or breaches the agreement? By having a Software Escrow arrangement, the end user ensures they’ll have access to a critical software application's source code and other essential materials if certain predefined conditions (known as "release conditions" or "release events") occur.
2. The vendor (the software developer/owner)
The vendor is the creator, developer, or owner of the software. Their intellectual property is at the core of their purpose and mission, so want to protect it while still meeting the needs of their clients. By participating in a Software Escrow agreement, the vendor demonstrates transparency and reliability, offering reassurance to the end user without compromising their IP. It’s a way to build trust while maintaining control over how and when the source code is accessed.
3. A trusted Escrow agent/provider.
The Escrow agent, such as SES Secure, is the neutral third party responsible for holding and safeguarding the source code and related materials. Their role is to ensure that the terms of the agreement are upheld impartially. They verify the integrity of the deposited materials, manage updates, and oversee the release process if a trigger event occurs.
In terms of the type of Software Escrow Agreement that’s implemented, this is determined by the specific needs and specifications of the client. For example, for a client seeking to safeguard a cloud-hosted software application, a SaaS Escrow Solution would be required.
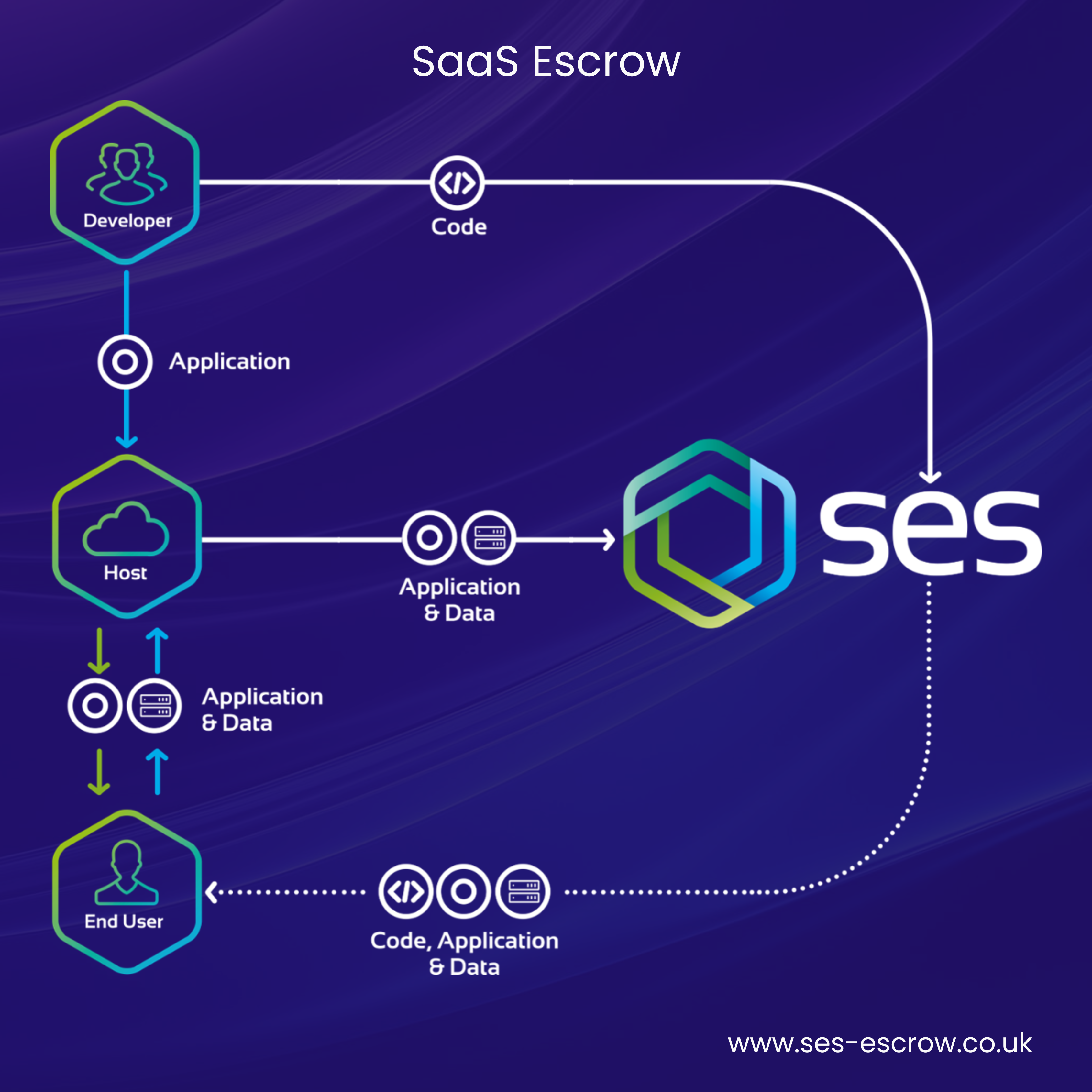
The Software Escrow Process at SES Secure
The first step of an SES Secure client's journey is an in-depth conversation with our team. This enables our team to clearly understand the client’s needs and consequently craft a bespoke solution that caters to all of the client’s various requirements. Following this, a Software Escrow solution is proposed.
Prior to the agreement being finalised, all parties will also collectively determine a set of release conditions under which the Escrow solution would be activated.
Following the agreement being agreed upon, the licensor deposits source code (source code is the foundation of any computer program) and other materials to SES Secure.
At SES, source code and other deposited materials are thoroughly tested by our in-house team of technological experts to ensure that they are accurate, up to date, and can be redeployed if required. These materials are then securely stored.
If release conditions are met, the source code and other relevant materials are released by SES to enable the end-user, allowing them to continue with the accessing, controlling, and operating a critical software application.
Ultimately, a Source Code Escrow Agreement provides extensive value and benefit to both software vendors and end-users. For businesses (end-users), the solution provides peace of mind though the presence of a comprehensive business continuity plan. It also puts assurances in place, ensuring that business operations can continue, regardless of unforeseen situations arising.

To see more reviews from our clients, check out our official Feefo page.
SaaS Continuity
Introduced by SES Secure in 2021, SaaS Continuity is a market-leading disaster recovery solution that offers unparalleled protection for mission-critical applications.
SaaS Continuity is purpose-built to ensure swift and uninterrupted access to cloud-hosted applications, even if the hosting environment or service provider becomes unavailable.
Something that separates SaaS Continuity from other services is the exceptional level of client convenience that it offers. When activated, the SES Secure team takes full responsibility for swiftly restoring the operational service on the client's behalf, followed by a guaranteed period of uninterrupted service continuity.
If you have any questions about anything in this blog or would like to speak to a member of our team, please don’t hesitate to get in touch.