If you're a software vendor or developer, chances are you've heard of Software Escrow, also known as Source Code Escrow. But if the term is new to you, diving into online resources can feel overwhelming. Much of the content out there is packed with technical jargon that can make the concept seem more complex than it really is.
This blog will look at the foundations of Software Escrow from a simple and easy-to-follow perspective. You may also want to take a look at another blog of ours, 'A Beginner’s Guide to Software Escrow'.
What is Software Escrow?
The terms ‘critical application’ and ‘mission-critical application’ refer to software applications and systems that play a pivotal role in a business’s ability to successfully operate.
For example, a critical application that an online retailer relies heavily on is its payment processing system. Now, if this system were to encounter operational disruption, numerous consequences could be experienced, such as:
- Damaged customer relationships.
- Financial loss.
- Reputational damage.
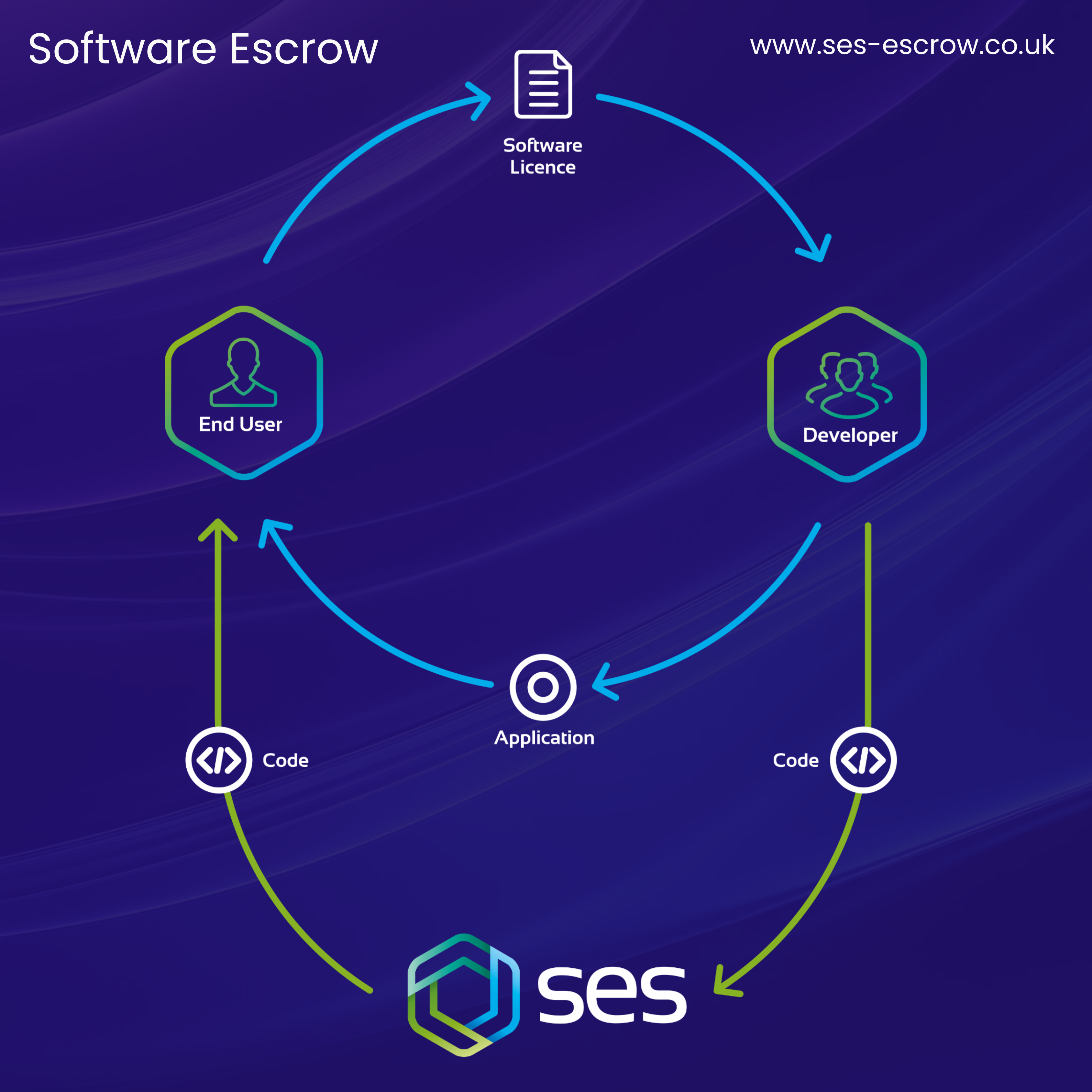
Let's return to the question of 'What is Software Escrow?'. Essentially, it’s a risk mitigation tool that addresses and combats third-party software vendor risk.
When it comes to critical applications, the term ‘software vendor’ refers to the application's owner or developer. Now, if an end user (i.e. a business or organisation) loses access or control over a critical application due to vendor failure or disruption, a Software Escrow Solution would enable the end-user to regain and maintain operational access over the application. This supports business continuity and operational resilience.
The Process of Setting Up and Activating a Software Escrow Solution
A Source Code Escrow agreement involves three parties:
- The End User (typically a business or organisation)
- The Vendor (a software application’s owner/developer)
- The Escrow Provider
Prior to the implementation of a Software Escrow Solution being finalised, the involved parties will establish a set of conditions under which an Escrow release event would occur. These conditions are referred to as ‘release conditions’ or ‘release events’. Common release conditions include a vendor going bankrupt, a vendor failing to maintain an adequate level of software delivery, a vendor breaching an agreement.
After the terms of a Software Escrow agreement have been agreed upon, the materials to be placed in Escrow (typically source code and other relevant materials) are deposited with SES. These materials are then tested to confirm that they’re accurate and can be redeployed successfully.
Following the testing process, the materials in Escrow are securely stored by SES. These materials are only released when a release condition has been met, causing an Escrow release event to be triggered.
In alignment with application updates, SES can take unlimited deposits of application data to ensure that end-users have accurate data in the event of a release.
On-Premises Vs SaaS Escrow
From its original introduction in the 1980’s up until the present day, the Software Escrow has evolved significantly.
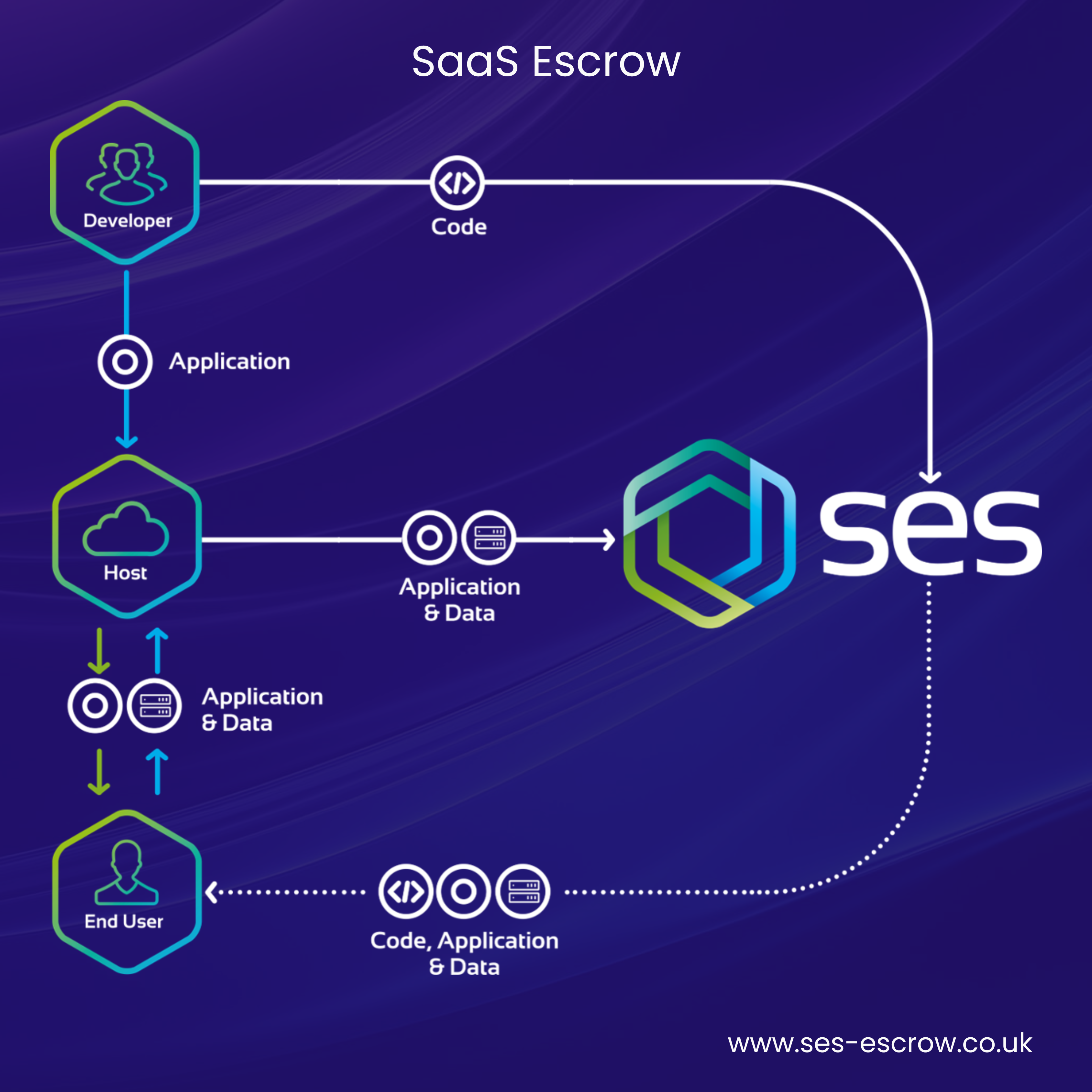
‘Traditional Software Escrow’ refers to a solution that safeguards applications that are physically installed on the premises of an organisation. However, as the popularity of the SaaS (cloud-hosted) software delivery model grew into what’s very much a dominant force in the present day, Software Escrow has also evolved to cater to SaaS applications.
Despite Software Escrow being able to form the foundation of a risk mitigation strategy for SaaS applications, there is still a prevailing misconception that Software Escrow doesn’t work with cloud-hosted applications. To learn more about this misconception, check out our blog, ‘SaaS Applications and Software Escrow – Can They Work Together?’.
Working with SES Secure
At SES, every client project is bespoke and completely tailored to the specific needs, preferences, and requirements of the client. Alongside this, communication and clarity are placed at the forefront. It’s crucial for us to ensure that all clients fully understand every step of their journey with us.
We also currently have over 200 verified reviews on Feefo – see them here.
If you have a question or would like to schedule a call with one of our experts, please don’t hesitate to get in touch.